Case 3: Are Multiple Anonymous threats from the same Author?
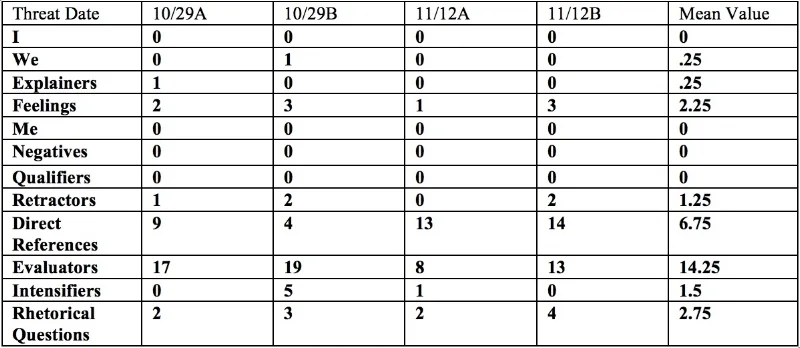
Another frequent profiling challenge involving cyber adversaries is the analysis of anonymous threats. Subjects seeking to extort payments from individuals and companies, terrorize or discredit former colleagues or seek revenge against organizations often use on-line channels to pursue their objectives. In addition to assessing the characteristics of these individuals, it is often important to understand whether multiple threat communications are from the same author. This is particularly important if the subject is pretending to send communications from different sources in an effort to magnify the appearance of the threat. Table 1 below displays the results of analysis of four anonymous threats sent to an organization in which the author-- -a suspected insider-- -threatened to reveal critical client information.
Table 1. Scores on Psycholinguistic Variables For Four Anonymous Threat Letters
The analytical tasks involved determining whether the letters were written by the same author and whether the psycholinguistic characteristics displayed in the notes were consistent with other materials produced by the suspected insider. When the four letters were compared several consistent patterns were noted indicating one author, including:
- The lack of use of personal pronouns (I, We, Me);
- The lack of use of negatives and qualifiers;
- The unusually high use of direct references and evaluators; and
- The unusually high use of rhetorical questions.
This distinctive pattern left little doubt that the letters were from the same source. These distinctive characteristics were then compared to a writing sample from a suspected insider, adding confirming data to support her identification. Data from the system was then utilized to compile a psychological profile of the suspect to assist in the management of her removal from the office and reduce the likelihood of damage to the organization and their clients. Related applications of WarmTouch with similar email threats have been used to study and then simulate the communication of adversary associates and design communications, based on profiling results, likely to be most effective with a specific cyber adversary.